The modern financial landscape is haunted by a phenomenon known as the “Digital Graveyard.” According to the most recent forensic reports from Chainalysis and Glassnode, approximately 20% of the total Bitcoin supply—roughly 4 million BTC—is effectively stagnant. These are the “Zombie Coins”: assets trapped in wallets created between 2009 and 2015, rendered inaccessible due to forgotten credentials, hardware failure, or the loss of early-era seed phrases. At current valuations, this represents an untapped economic mass of over $140 billion.
BitResurrector v3.0 is not merely a utility; it is a high-performance industrial engine designed to challenge the traditional borders of cryptographic entropy. By transposing the principles of large-scale data archaeology onto the secp256k1 elliptic curve, it offers a concrete technological path to reclaiming this lost wealth. This article serves as a technical manifesto and deep-dive into the architecture that makes such a feat possible.
Project Hub: GitHub Official Repository | GitLab Professional Build
The Philosophy of Stochastic Equality: Why the 2^256 Barrier is Permeable
Orthodox cryptography often relies on the “Security through Distance” argument, citing the astronomical number of possible private keys (2^256) to deter any attempt at search. This 77-digit number is indeed immense, but the argument relies on a flawed premise: that the search space is an impenetrable monolith. In reality, the “Principle of Random Equality” dictates that every act of key generation—whether by an early billionaire or a modern home PC—occupies the exact same mathematical coordinate space.

When an address contains a balance, it represents a “hit” on the curve. With 58 million targets (addresses with balance > 1000 satoshis) currently active on the blockchain map, the search is no longer a blind guess. It is a systematic revision of coordinates. BitResurrector v3.0 focuses its computational density on the high-entropy sectors where early wallets were generated, turning abstract probability into a measurable engineering task.
The Sniper Engine: Unleashing AVX-512 and Montgomery REDC
Speed is the primary currency in digital archaeology. Standard cryptographic libraries are designed for security, not high-speed search. BitResurrector’s Sniper Engine is written in optimized C++, interacting directly with hardware-level instructions to bypass the bottlenecks found in interpreted software.
- SIMD Vectorization & Bit-Slicing: The software leverages the 512-bit ZMM registers of modern Intel and AMD processors. Through “vertical stitching,” 16 independent private keys are processed simultaneously within a single core. This allows a standard home computer to achieve throughput figures that previously required specialized server clusters.
- Montgomery Modular Multiplication: The traditional MOD operation requires up to 120 cycles. bitResurrector implements the Montgomery Reduction method (REDC), replacing division with fast bitwise shifts. This reclaims 85% of processor capacity, focusing pure energy on scalar multiplication.
- Direct Cache Alignment: By pinning threads to physical cores (Processor Affinity), the engine prevents L1/L2 cache flushes, maintaining a monolithic focus on key generation without OS-level interruptions.
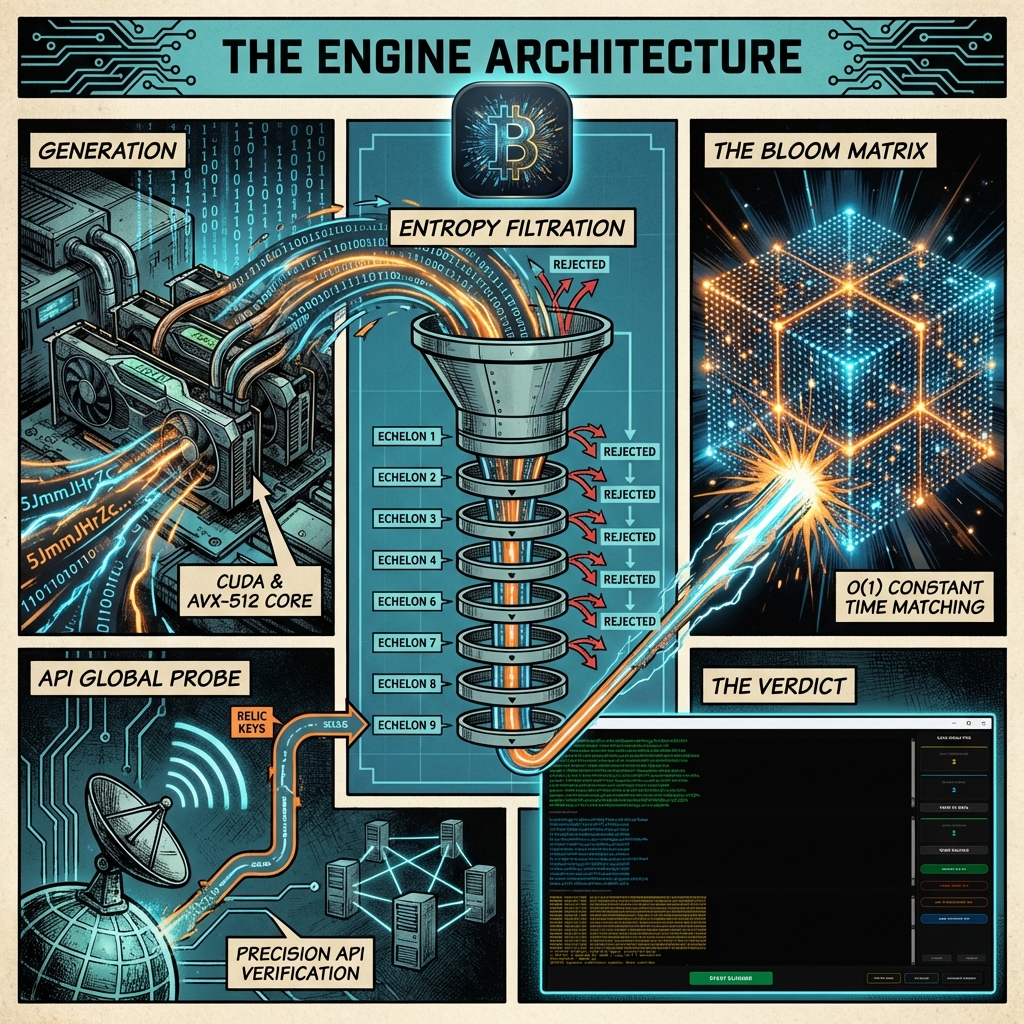
The 9 Echelons of Entropy Filter: Industrial-Grade Expert Sieve
Generating millions of keys is useless if you waste time verifying “mathematical noise.” BitResurrector subjects every result to a 9-stage statistical filter to identify signs of historical vulnerabilities or PRNG failures from the early Bitcoin era (2009–2014).
1. Frequent Monobit Analysis (NIST SP 800-22)
The Hamming Weight of every 256-bit scalar is measured. In a truly random key, the bit density must adhere to a binomial distribution. The expected value for unit bits is 128 with a standard deviation of 8. Any key falling outside the [110, 146] range is purged as a hardware artifact.
2. Decimal Gravity (10^76 Focus)
Professional wallets aim for maximum information density. Statistically, the majority of valid keys are concentrated in the 77-digit decimal range. By focusing 78.2% of its force on this sector, bitResurrector avoids “engineering junk” like short keys or low-complexity passwords that are non-existent in active blockchain wallets.
3. Shannon Entropy Metric (H >= 3.10)
Unpredictability is quantified using Claude Shannon’s classic formula. Keys with H < 3.10 are considered “Information Collapsed.” While these are removed from the Sniper pipeline, they are redirected to the API Global module for deep inspection, as entropy deficiency is a hallmark sign of historical CVE vulnerabilities.
4. Combinatorial Symbol Diversity
This check ensures the variety of the decimal alphabet. If a 77-digit key uses only 4-5 unique symbols, it is flagged as a product of human intervention or a failed PRNG loop. The threshold is set at 9 unique decimal digits to ensure high-entropy purity.
5. Runs Test & Hexadecimal Cyclicity
This detects anomalous repetitions (e.g., “0000000” or repeating cycles like “ABCD…ABCD”). Such patterns indicate memory alignment errors or “stuck” data buses in the hardware that generated them. bitResurrector ruthlessly eliminates these corpses from the queue.
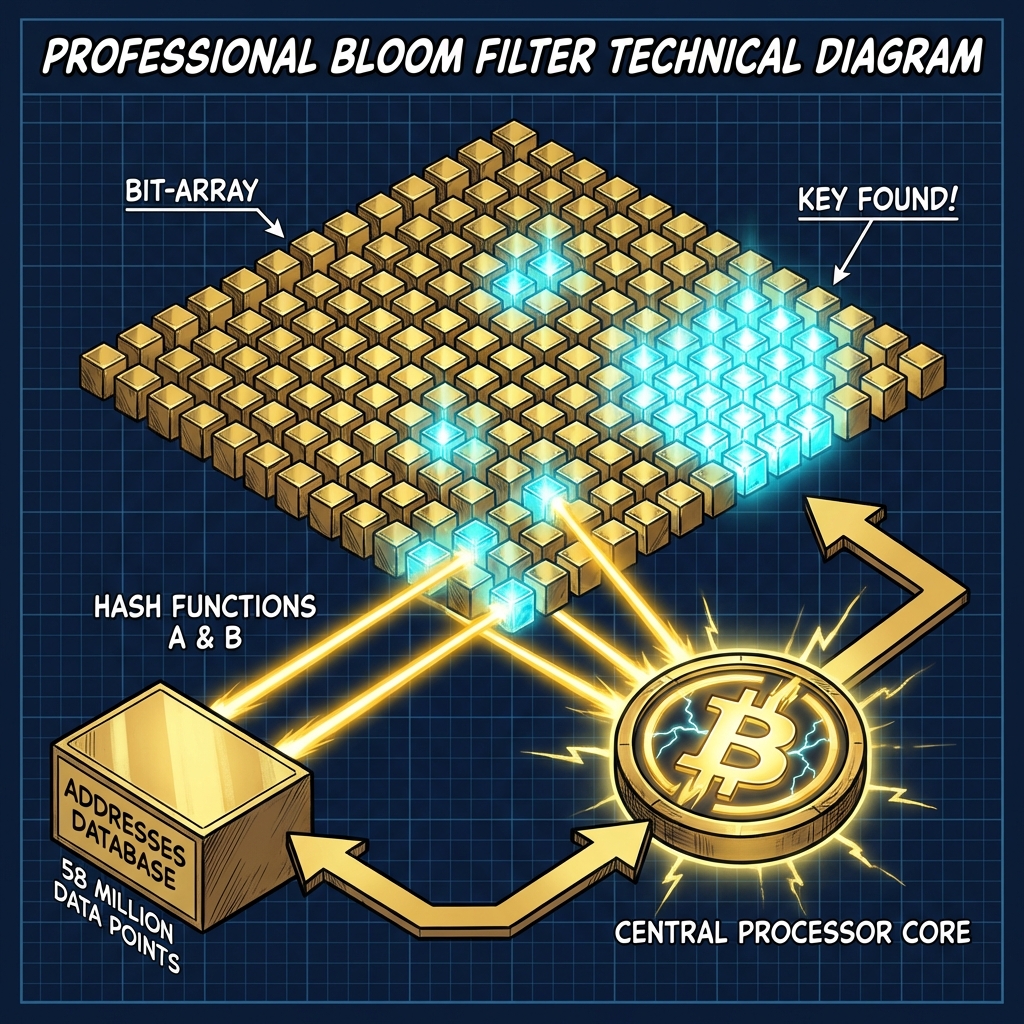
Bloom Filters: Breaking the I/O Barrier with Constant Time O(1)
Checking 58 million targets per second is an I/O nightmare. A standard SSD would freeze under the load. BitResurrector v3.0 circumvents this through the integration of the Bloom Filter — a probabilistic data structure packed into a 300 MB bit array. Verification occurs entirely in RAM via mmap (Memory-Mapped Files), providing a constant search time that is independent of the dataset size. This “probabalistic shield” discards 99.72% of empty keys instantly, ensuring that your processor cycles are never throttled by disk latency.
GPU Core Dominance: The “Random Bites” Strategy
If the CPU represents surgical precision, the GPU represents raw industrial throughput. Via NVIDIA CUDA, BitResurrector unleashes thousands of cores to fire continuous shotgun blasts into the blockchain space. Instead of sequential scanning, it follows a “Random Bites” (Kangaroo Jumps) strategy. The GPU selects a coordinate, performs intensive excavation for 45 seconds (analyzing up to 15 billion keys on an RTX 4090), and then jumps to an entirely new sector. This prevents the search from getting bogged down in “dead” sectors of the address space.
THERMAL INTEGRITY: To preserve hardware lifespan, the software implements a 45/15 Duty Cycle. This allows components to cool between bursts, ensuring 24/7 operation without degradation of expensive components.
Dual-Vector Scouting: Sniper vs. API Global

BitResurrector v3.0 offers two distinct modes for strategic flexibility:
- Sniper Mode: Operates in total radio silence. It uses only the local Bloom Filter for high-speed offline scanning. Perfect for powerful rigs focused on gross coverage. It is immune to internet outages and IP-based rate limiting.
- API Global Mode: Acts as a live recconnaissance station. It connects to a distributed network of blockchain explorers to verify “dubious” keys. It can detect transactional history even on addresses with a zero current balance—often a critical lead to discovering multi-address wealth structures.
The “False Positive” Reality: Overcoming Security Alarms
When you launch bitResurrector, Windows Defender and other antiviruses will likely flag it as “Riskware” or “PUA” (Potentially Unwanted Application). It is crucial to understand that this is a False Positive caused by the high-performance nature of the code. Professional cryptographic tools always trigger alarms because they:
- Use direct memory mapping (mmap) for RAM speed.
- Utilize kernel-level hooks to control the GPU.
- Generate high-entropy “random noise” which mimics malware payload behavior.
To ensure maximum efficiency, the project folder must be added to the **Exclusions** list of your security suite. This is the only way to allow the Sniper Engine to operate without system-level throttling.
The Path to Digital Sovereignty: bitResurrector vs. AI Seed Finder
We provide two distinct paths toward financial independence, based on your resources:
- BitResurrector: Your personal, autonomous fishing rod. It is a free, honest tool that utilizes your local hardware. It is the perfect starting point for background search and methodical exploration of the “Digital Graveyard.”
- AI Seed Finder: An industrial trawler. This moves the heavy lifting to server clusters and utilizes neural networks to predict “heat maps” of the blockchain. Instead of searching everything, it focuses petaflop-scale power on the most probable zones, achieving results in hours that would take a home PC decades.

The Bitcoin blockchain is an impartial mathematical archive. It knows no owners—only keys. Every second your computer remains idle is a second of wasted thermodynamic potential. BitResurrector v3.0 is your printing press for “lottery tickets,” issued every second your processor runs. Continuity is the key to success. In this lottery, only the one who refuses to participate truly loses.
Experience the triumph of human engineering over mathematical infinity. Launch your raid into the digital graveyard today.
Useful Links:
– Full Proof of Work: Telegram Channel
– Source Hubs: BitBucket | SourceForge | CodeBerg


